Removing hidden kill switches in your renewable energy portfolio
As renewable energy systems become more connected and data-driven, they also become more exposed. Hidden remote-access features, unmonitored firmware updates, and complex vendor ecosystems can turn a solar or wind portfolio into a cybersecurity minefield. This article explores how “trusted technology” can be turned against operators, why new EU regulations like NIS2 and the Cyber Resilience Act make proactive protection essential, and how Helin’s “one box” approach restores control, visibility, and compliance across your energy portfolio.

The new frontline of energy security
In the renewable energy sector, digitalization has become both a blessing and a potential Achilles’ heel. As renewable energy infrastructure becomes increasingly interconnected, it simultaneously become more exposed to cyber risks.
Recent years have seen a dramatic rise in cybersecurity incidents targeting critical infrastructure. From ransomware attacks that shut down pipeline operations to malware that disrupted power grids, the energy industry is facing a new class of threats - ones that can halt production, corrupt data or even take control over assets remotely.
At the same time, new European mandates such as NIS2, the Cyber Resilience Act (CRA), and the Data Act are reshaping the responsibilities of operators. Compliance is no longer optional; it’s fundamental to business continuity. Yet, many renewable operators lack the in-house IT and OT expertise to keep pace.
This article outlines how to regain control - both technically and operationally - and how to eliminate the hidden kill switches that might already be buried deep inside your assets.
When “Trusted Technology” turns against you
Many renewable energy operators assume that the technology embedded in their assets is safe simply because it comes from reputable vendors.
Unfortunately, this isn’t always the case.
Today’s inverters, loggers, and communication modules often ship with factory-installed remote management features. These can include diagnostic channels, firmware update paths, or cloud “support tunnels” that is often not aware of and does not have full control over.
In 2024, an inverter manufacturer remotely shut down thousands of inverters across multiple countries amid a commercial dispute. Investigations showed that some hardware contained undocumented communication modules, capable of bypassing local firewalls. This incident confirmed what cybersecurity researchers had warned: remote kill switches do exist, and they are being used. (Source: Rogue communication devices found in Chinese solar power inverters | Reuters)
It’s not only hidden kill switches that create the risk of being locked out of your assets, resulting in huge negative returns. In 2025, a case in the Netherlands showed how vulnerable operators can be: a firmware update was pushed by the OEM without prior communication. As a result, the trading department lost control over production and became exposed to negative electricity prices on the spot market — without any ability to curtail their load.
The regulatory squeeze
.png)
Regulators are taking notice. Under NIS2, energy companies must implement risk management, incident reporting, and supply chain oversight. The CRA goes further, making manufacturers accountable for vulnerabilities in connected products.
Operators can no longer rely on EPCs or O&M partners to resolve this, as their expertise lies in performance and reliability of energy assets, not cybersecurity. As a result, renewable companies need to take charge of their digital perimeter. Failing to do so risks compliance failures, reputational damage, and worst of all, operational lockouts.
Site fragmentation growing with each partner
The risk lies not only in malicious intent but also in poor design and supplier opacity. Operators often inherit black-box systems where visibility ends at the user interface. Worse, many portfolios consist of fragmented hardware ecosystems, with each partner managing their own edge device to connect to assets remotely, either for Data Management, Remote Control and/ or Remote Access.
New devices get added: protocol converters, loggers, firewalls, cloud connectors. Before long, the asset becomes a nest of vendor-specific devices with the added risk of vulnerabilities.
What’s manageable today becomes uncontrollable tomorrow.
Helin’s solution:
This is where the Helin Smart Grid Manager comes in. Helping you face these challenges by simplifying and centralizing energy and asset management across your organization, and giving you a full audit trail of events with Helin’s linked services, compliance with NIS2 and the cyber security resilience act.
One safe box
Helin provides all essential energy and asset management functions for site operations within one unified device. This restores your Single Source of Truth and allows you to give all of your partners the exact access and control rights they need. No more, no less.
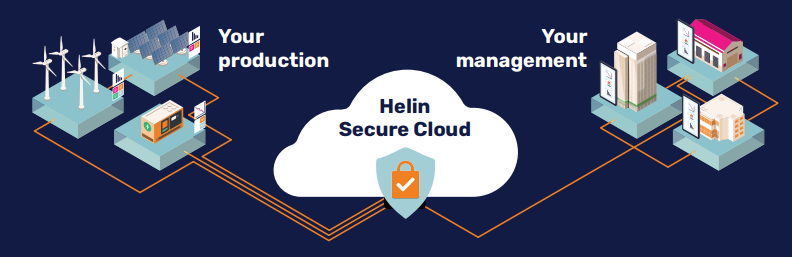
By centralizing all functionalities, we create one secure outbound connection from the site to you and your partners’ cloud endpoints. This removes hidden kill switches, gives you full ownership of partner integrations, and ensures 100% visibility across the entire operational value chain.
Key functions within one secure device (amongst other):
Security
- Secure (Zero Trust) Remote Access tunnels
- Fully encrypted data and control signals
- Cloud-based site traffic filtering
- Local network scanning
Data & Control
- End to end data management, from capture to insights
- Real-time remote control to any trading desk, including real-time diagnostics and asset telemetry
- Local control logic and full EMS functionality
All in one device — organized, safe, and fully under your control.
Cloud based site traffic filtering
To extend your site's security and eliminate any unwanted access to your site, Helin has a cloud-based Firewall that filters all traffic that goes in and out of your sites. This way only predefined destinations (ACL) will be allowed, and any rogue connections will be identified and blocked. It is created such that even in legacy situations we can route all traffic through our backbone and filter out any unwanted events.
Local network scanning & tinkering
Even if traffic is not going out, it might be trying to compromise devices from within. This is why we offer real-time scanning of your local network to detect any malicious activity. Combined with alarming on physical tinkering of your devices, you are protected against the lowest level of intrusion.
One center, real-time security
Even with a hardened architecture, visibility is key. We can help you set up a security center with 24/7 monitoring and alerting, in-house or as a service. This center will give you real-time insight into threats, activity and status of your system.
Six no-nonsense rules for keeping your systems secure:
- Restrict and separate networks. No internet and less interconnections mean less risks. Use both inbound and outbound filtering.
- Use layered access roles and allow only the necessary.
- Security is partly technical but moreover it's human. Don't overcomplicate so people will bypass things - that's even more dangerous.
- Use encrypted communications. Always. Everywhere. No ftp no http.
- Keep your systems up to date - but be in charge. Have a change management process in place and be aware of automatic updates.
- Implement network monitoring and threat scanning.
The one box principle
Each asset becomes part of a standardized, transparent management environment.
According to a deployment at Sunrock, this approach led to:
- Faster onboarding of new assets
- Unified monitoring across renewable energy infrastructure
- Elimination of insecure legacy hardware
- Efficient on- and offboarding of partners
- Complete oversight and control across the entire value chain of assets
Why hidden kill switches are everyone’s problem
This is not just about malicious backdoors. It's about architecture. When remote devices and data paths are outside your domain, you can't secure what you can't see.
Helin’s model reclaims visibility and control through standardization, staging, segmentation, and security monitoring.
NIS2 will enforce much of this by law. Operators who act now will gain not just compliance, but resilience.
From awareness to action
Start with the fundamentals. Then consolidate the edge. Then monitor it continuously.
- Standardize with the One Box Principle
- Validate with firmware staging
- Protect with segmentation
- Detect with continuous and autonomous monitoring
- Oversee with a managed Security Operations Centre
Together, these layers form your digital defense against tomorrow’s disruptions.
Conclusion: Take back control
Hidden kill switches don’t announce themselves. But you can remove them before they strike.
With Helin’s cybersecurity framework, you regain control over every update, connection, and decision inside your portfolio.
One box. Total control. Zero compromise.
👉🏻 Talk to our experts
We’ll help you assess your edge architecture, identify blind spots, and secure your renewable operations, before someone else does.
Want to read more?
Stay up to date with the latest trends and developments on the topic of industrial edge computing, monitoring and intelligence.
Get real-time insights
into your remote assets
Combine local artificial intelligence with a centrally managed data infrastructure for more accuracy, reduced congestion on your network and lower costs.



%20(1).png)
%20(1).png)







